Struggling to set up PureVPN on Linux Parrot devices? Look no further. Our comprehensive and user-friendly guide will assist you in configuring PureVPN effortlessly, ensuring you can connect and maintain online security with ease on your Linux Parrot supported devices.
Find your VPN credentials for manual configuration
To find your VPN credentials log into the PureVPN member area. Click 👉 here to visit Member Area.
Login to the Member Area using your PureVPN registered email address and password.
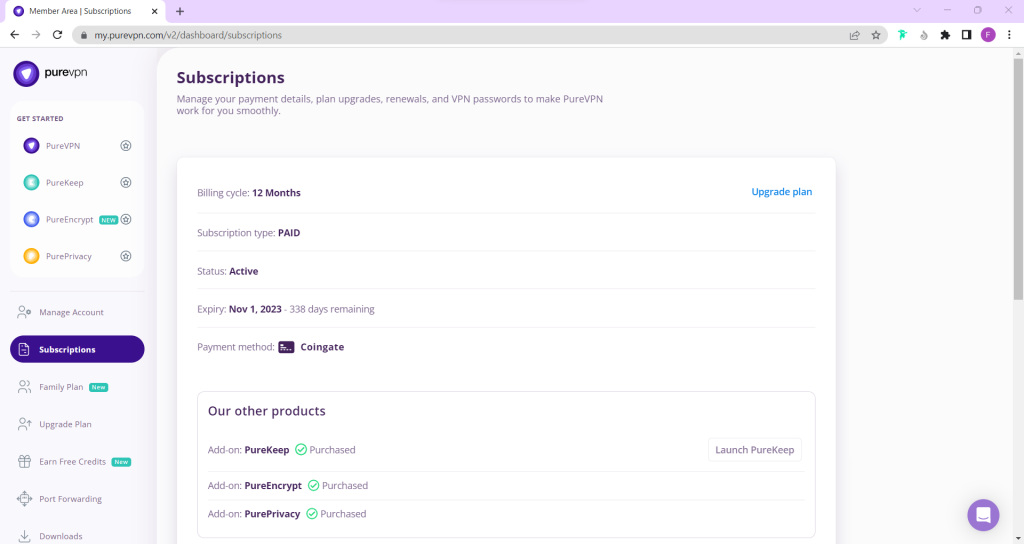
On Subscription tab scroll down to be able to view your VPN credentials.
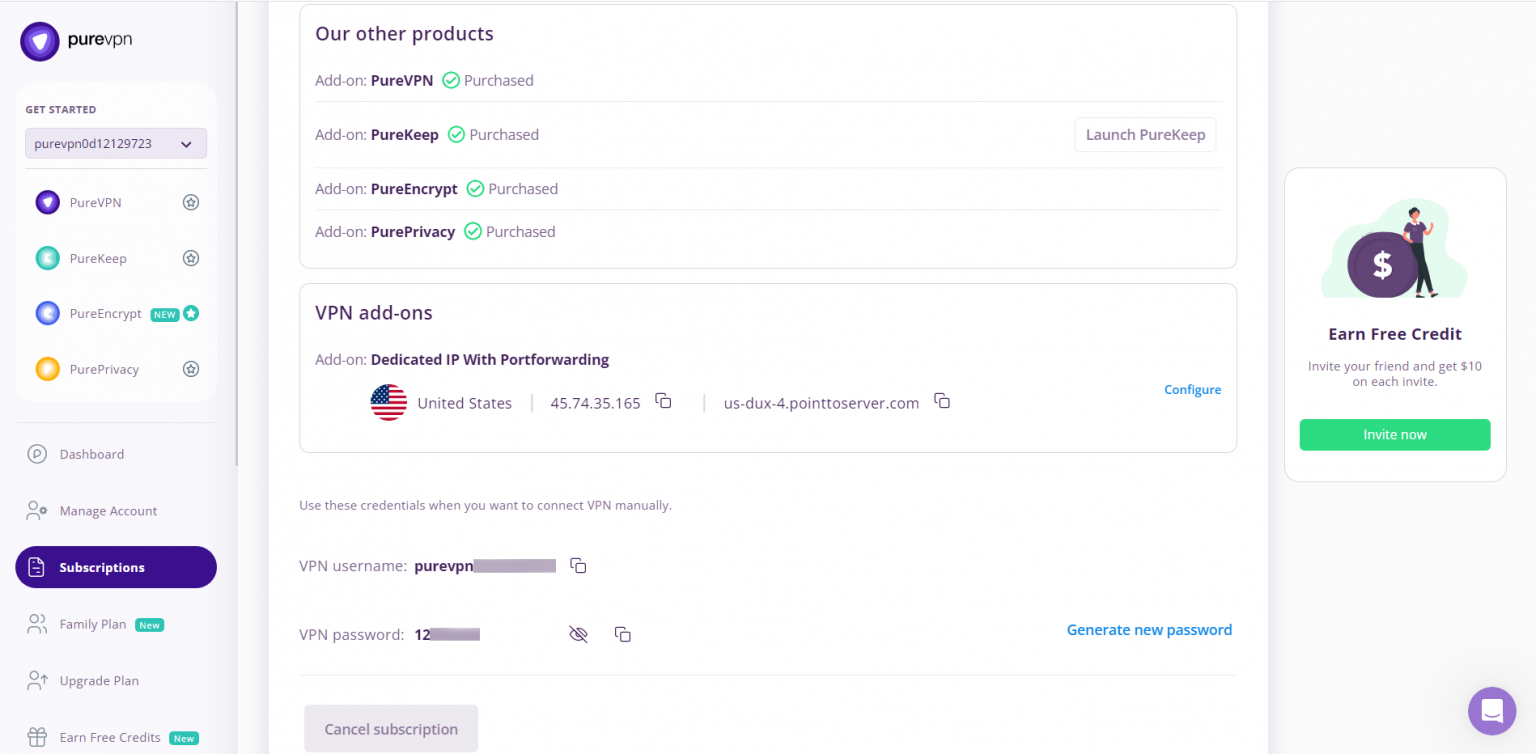
- You will be able to see and copy your VPN credentials.
- Note down your PureVPN username and click the Eye icon to make your password visible and use it in the manual configuration.
How to connect PPTP on Linux Parrot OS 5.0
- Go to the Terminal window and type the following commands one by one:
- sudo apt-get update
- sudo apt-get install pptpd
-
Now Select the following options:
- Click Wired Connection.
- Go to VPN Connections.
- Select Add a VPN Connection.
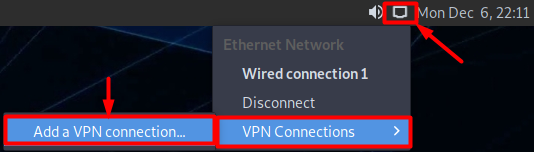
- Select Point-to-Point Tunneling Protocol (PPTP) option from the list and then click Create button.
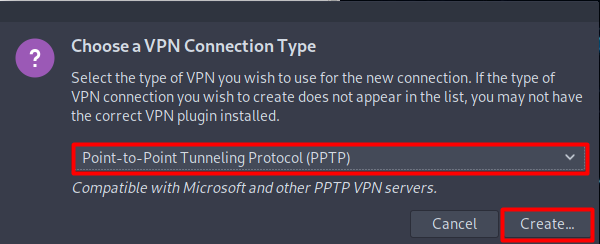
- When a new window appears, complete the fields as below:
- Connection name: PureVPN
- Insert the desired server: These servers can be utilized for the PPTP protocol.
- Germany: de1.pointtoserver.com
- Netherlands: nl1.pointtoserver.com
- United Kingdom: ukl1.pointtoserver.com
- United States: ustx1.pointtoserver.com
- United States: uswdc1.pointtoserver.com
- Australia: au-sd1.pointtoserver.com
- Enter your VPN credentials. Here is how you can find your VPN credentials.
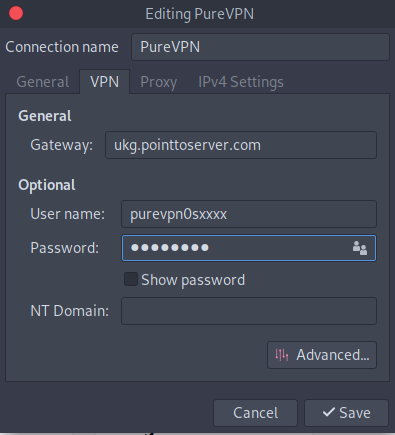
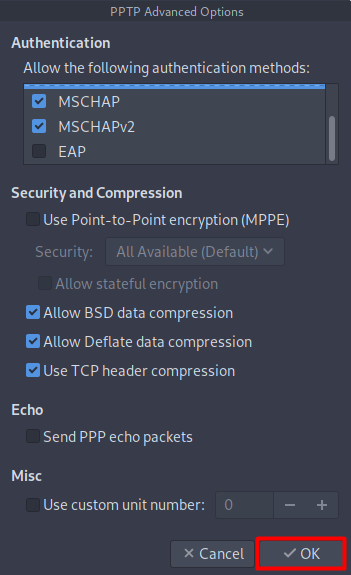
- Now, go to the Advanced option.
- Only check/ Allow the following options.
- MSCHAP.
- MSCHAPV2.
- Also, select the following:
- Allow BSD data compression.
- Allow Deflate data compression.
- Use TCP header compression.
- Click OK and then click Save button.
- Now go to the Wired Connections option and under VPN Connections click the newly created PureVPN connection to activate the VPN connection.
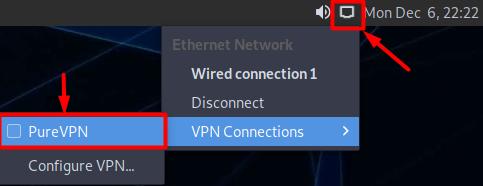
- You are connected now!

How to connect L2TP on Linux Parrot OS 5.0
- Go to the Terminal window and type the following commands one by one:
- sudo apt-get update
- sudo apt-get install xl2tpd
- sudo apt-get install network-manager-l2tp
- sudo apt-get install network-manager-l2tp-gnome
-
Now Select the following options:
- Click Wired Connection.
- Go to VPN Connections.
- Select Add a VPN Connection.
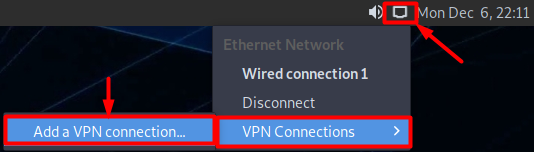
- Select Layer 2 Tunneling Protocol (L2TP) option from the list and then click Create button.
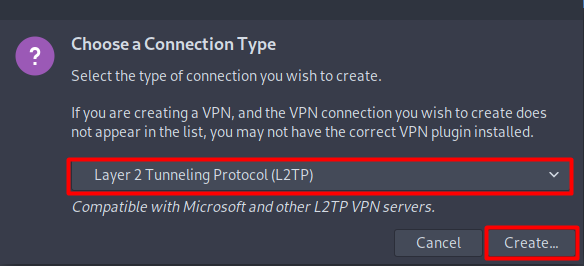
- When a new window appears, complete the fields as below:
- Connection name: PureVPN
- Insert desired server address in Gateway (Here we have used ukg.pointtoserver.com)
- Enter your VPN credentials. Here is how you can find your VPN credentials.
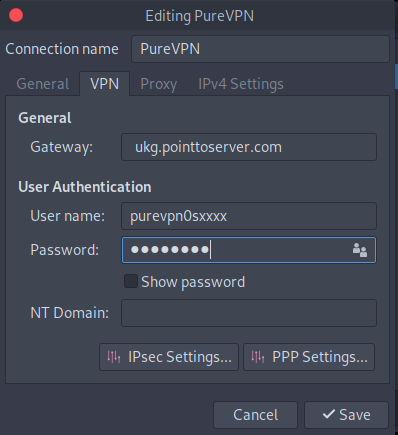
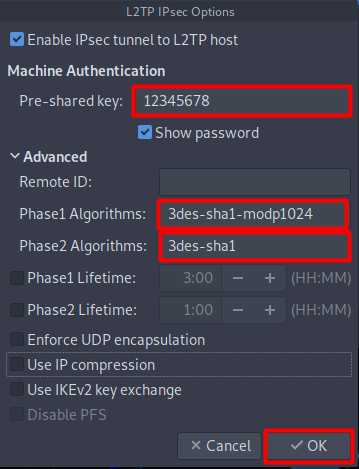
- Now, go to the IPsec Settings button.
- Check the Enable Ipsec tunnel to IPsec host
- Pre-share key: 12345678
- Under the Advanced section, specific the connection algorithms:
- Phase 1 algorithms: 3des-sha1-modp1024
- Phase 2 algorithms: 3des-sha1
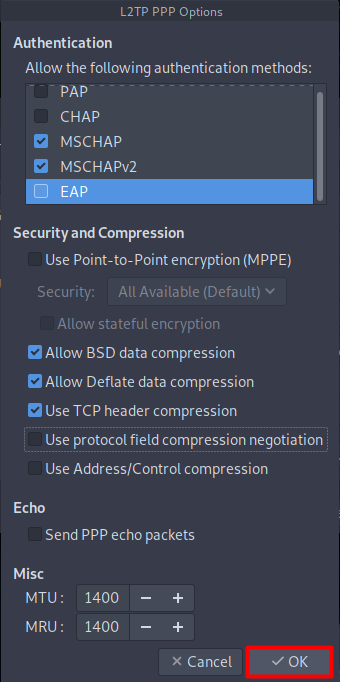
- Click OK.
- Now, go to the PPP Settings button.
- Only check/ allow the following options:
- MSCHAP.
- MSCHAPV2.
- Also, select the following:
- Allow BSD data compression.
- Allow Deflate data compression.
- Use TCP header compression.
- Click OK and then click Save button.
- Now go to the Wired Connections option and under VPN Connections click the newly created PureVPN connection to activate the VPN connection.
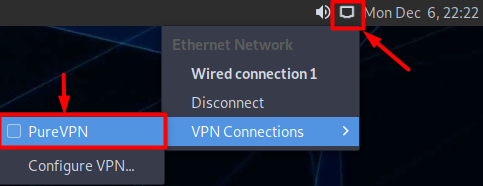
- You are connected now!

How to connect OpenVPN on Linux Parrot OS 5.0
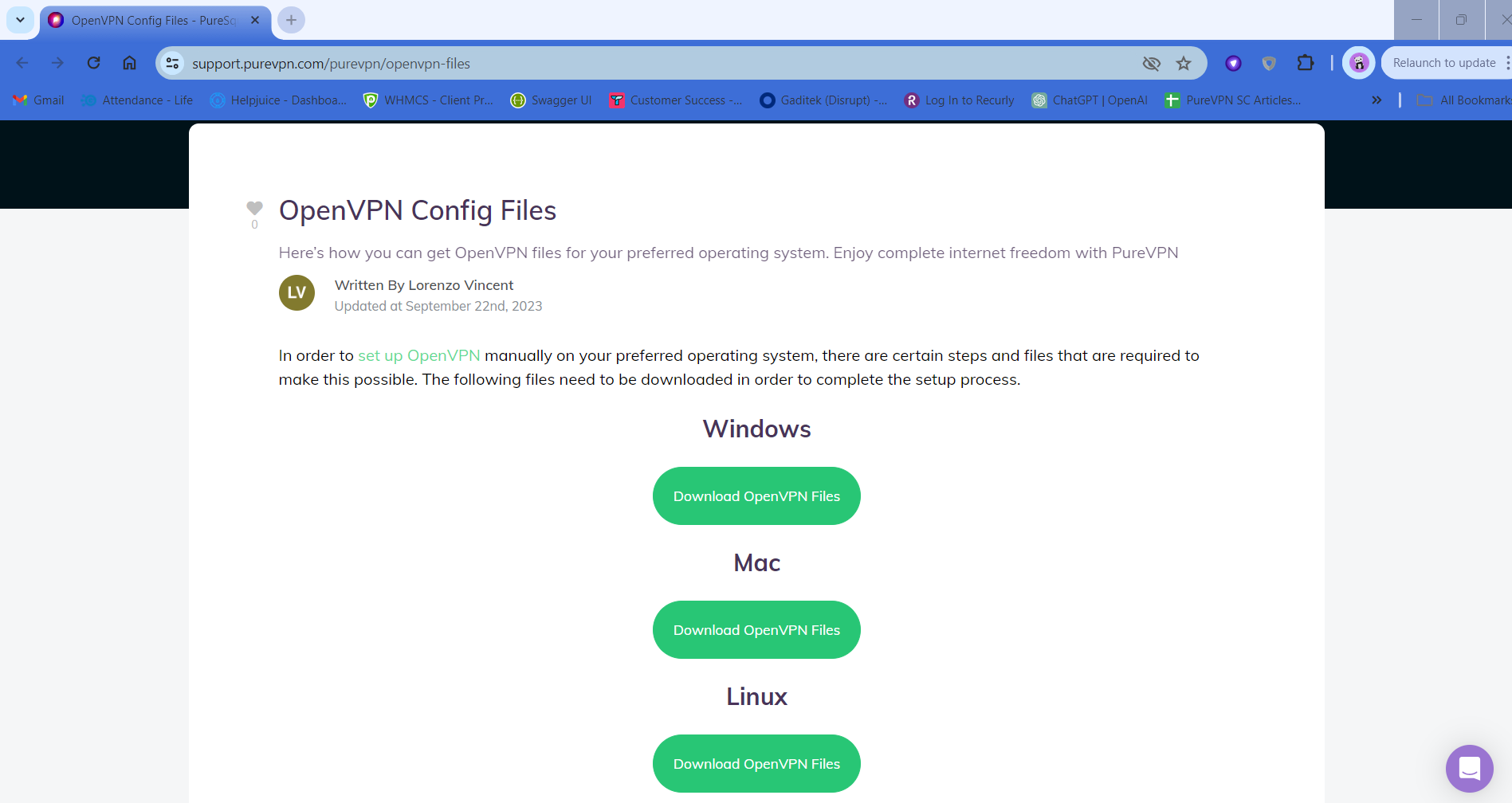
As a first step, it is recommended to download the OpenVPN config files for that you can go to your desired web browser, download PureVPN OpenVPN configuration 👉 files, and extract them.
- Go to the Terminal window and type the following commands one by one:
- sudo apt-get update
- sudo apt-get install openvpn
- sudo apt-get install network-manager-openvpn
- sudo apt-get install network-manager-openvpn-gnome
-
Now Select the following options:
- Click Wired Connection.
- Go to VPN Connections.
- Select Add a VPN Connection.
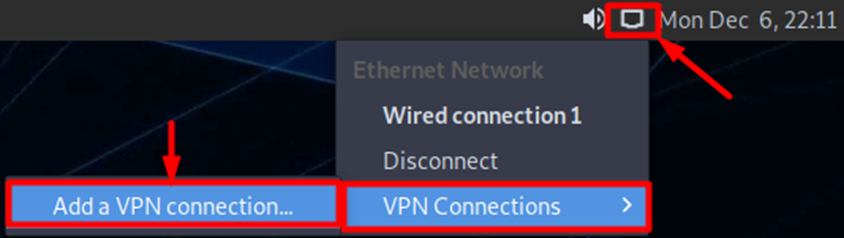
- Select Import a saved VPN configuration. option from the list and then click Create button.
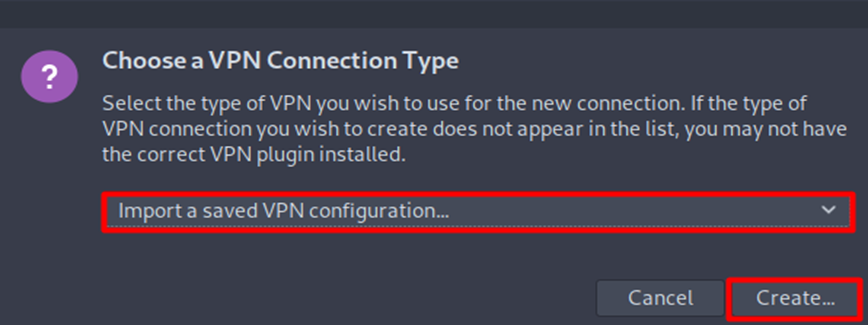
- Go to the folder where you have downloaded the OpenVPN files and select your desired .ovpn file to connect.
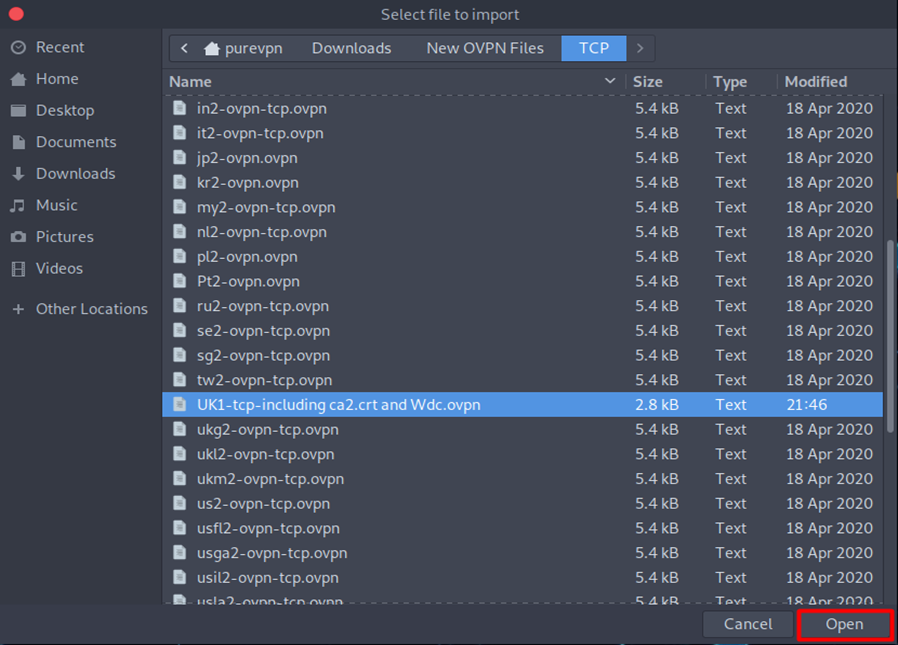
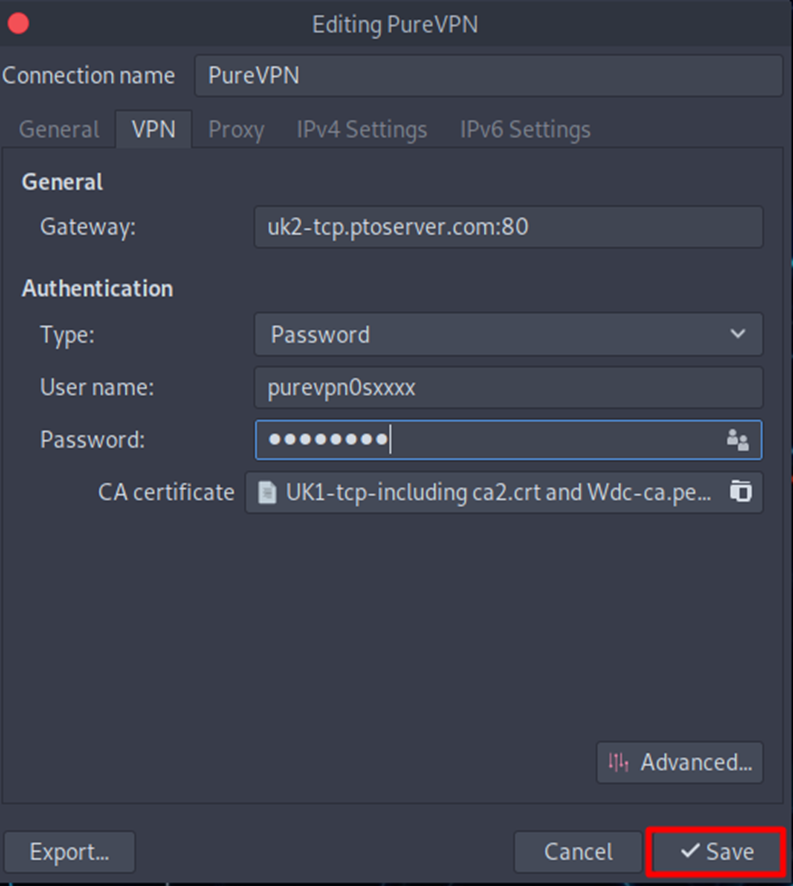
- When the new window appears, complete the fields as below:
- Insert Connection name: PureVPN
- Insert Gateway: (already selected/entered)
- Connection Type: Password from drop down menu
- Enter your VPN credentials. Here is how you can find your VPN credentials.
- CA Certificate: Already uploaded.
- Click Save button.
- Now go to the Wired Connections option and under VPN Connections click the newly created PureVPN connection to activate the VPN connection.
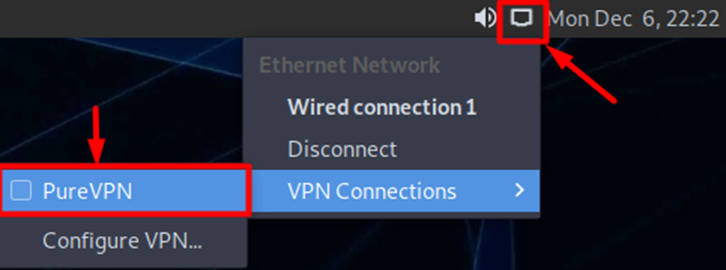
- You are connected to PureVPN now!

