To access PureDome applications, users have the option to verify their identity using Okta Single Sign-On (SSO).
How to enable Okta SSO?
Below are the steps to configure Okta SSO integration:
Step 1 - Setting up SSO Application on Okta
- Log in to Okta and navigate to the Admin panel.
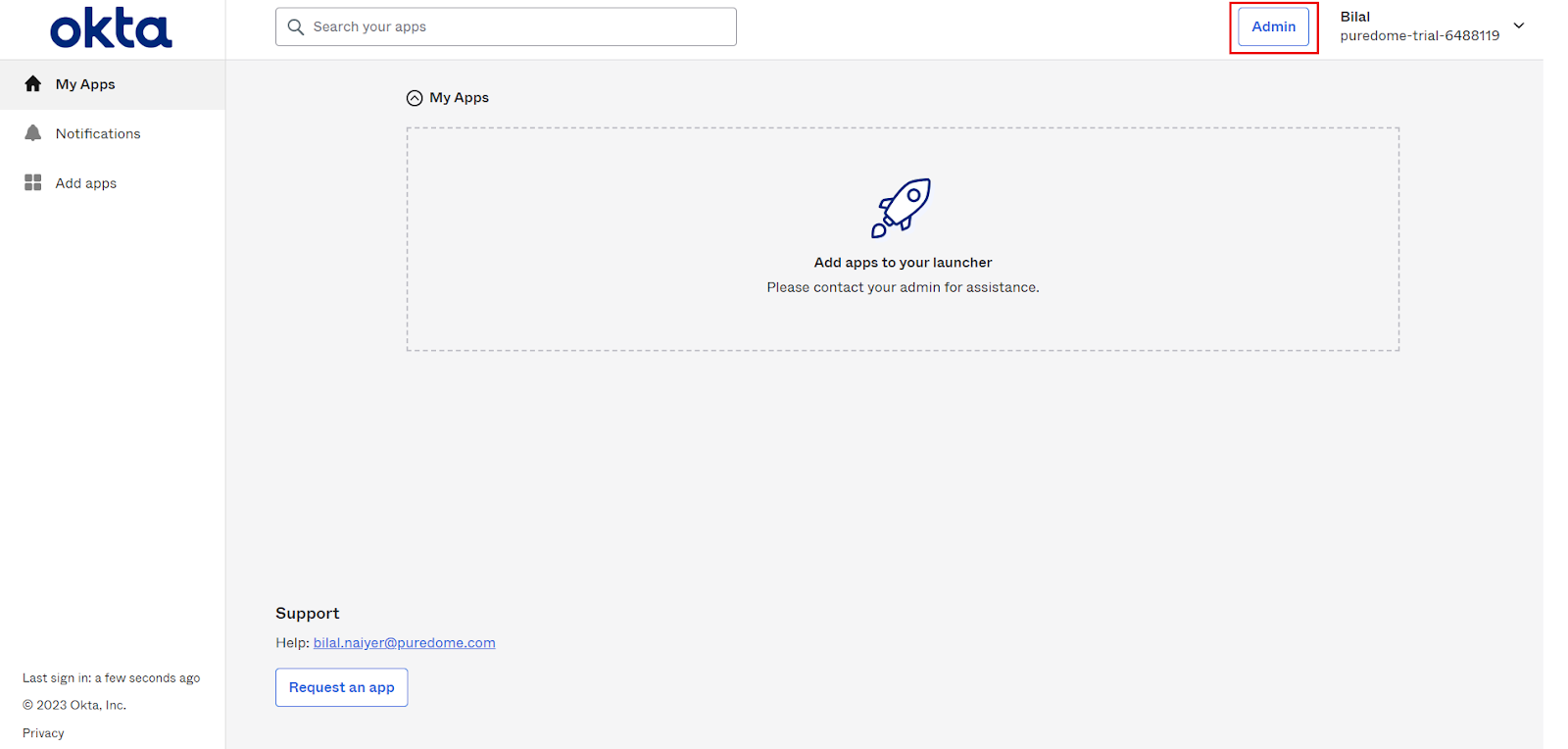
- Navigate to Applications > Applications and click the Create App Integration button.
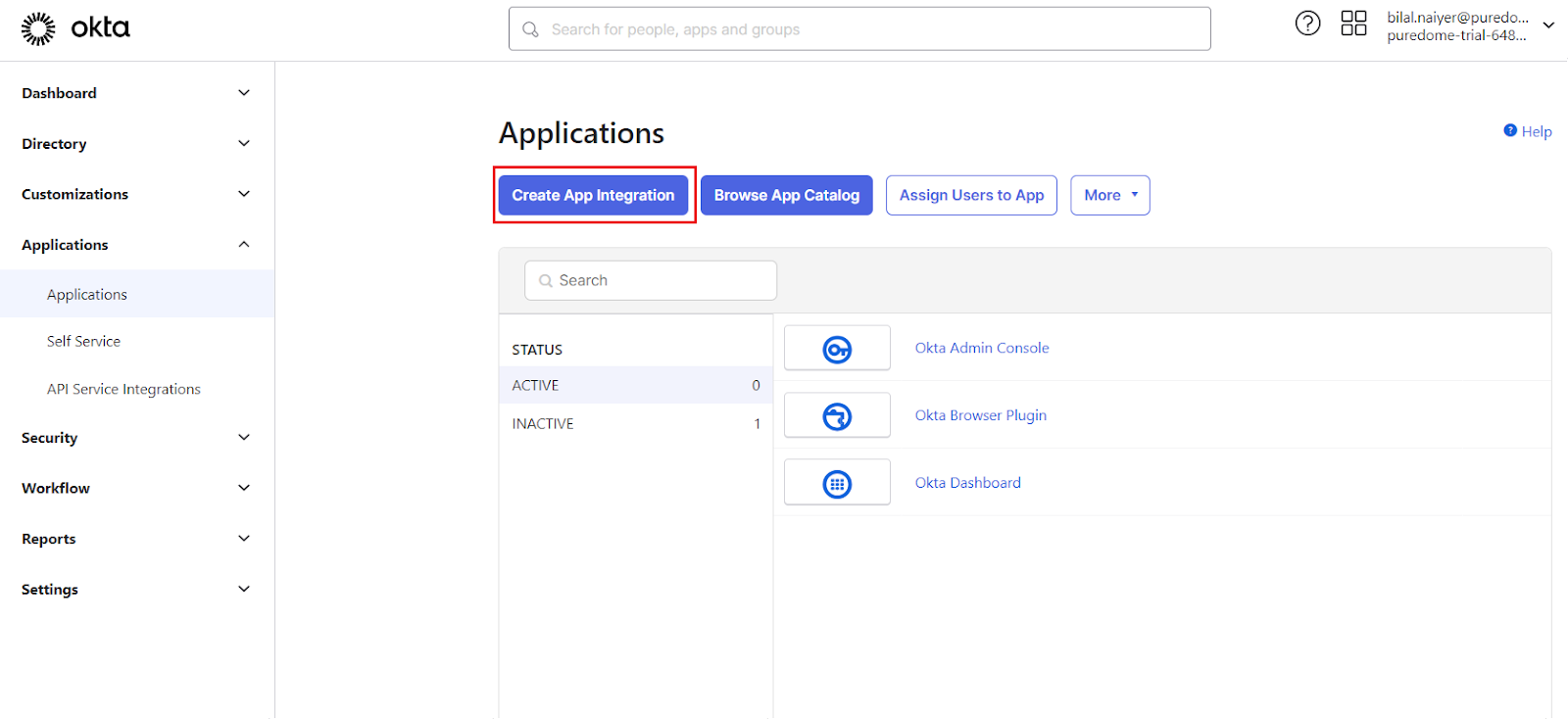
- Select OIDC - OpenID Connect and Web Application and then click Next.
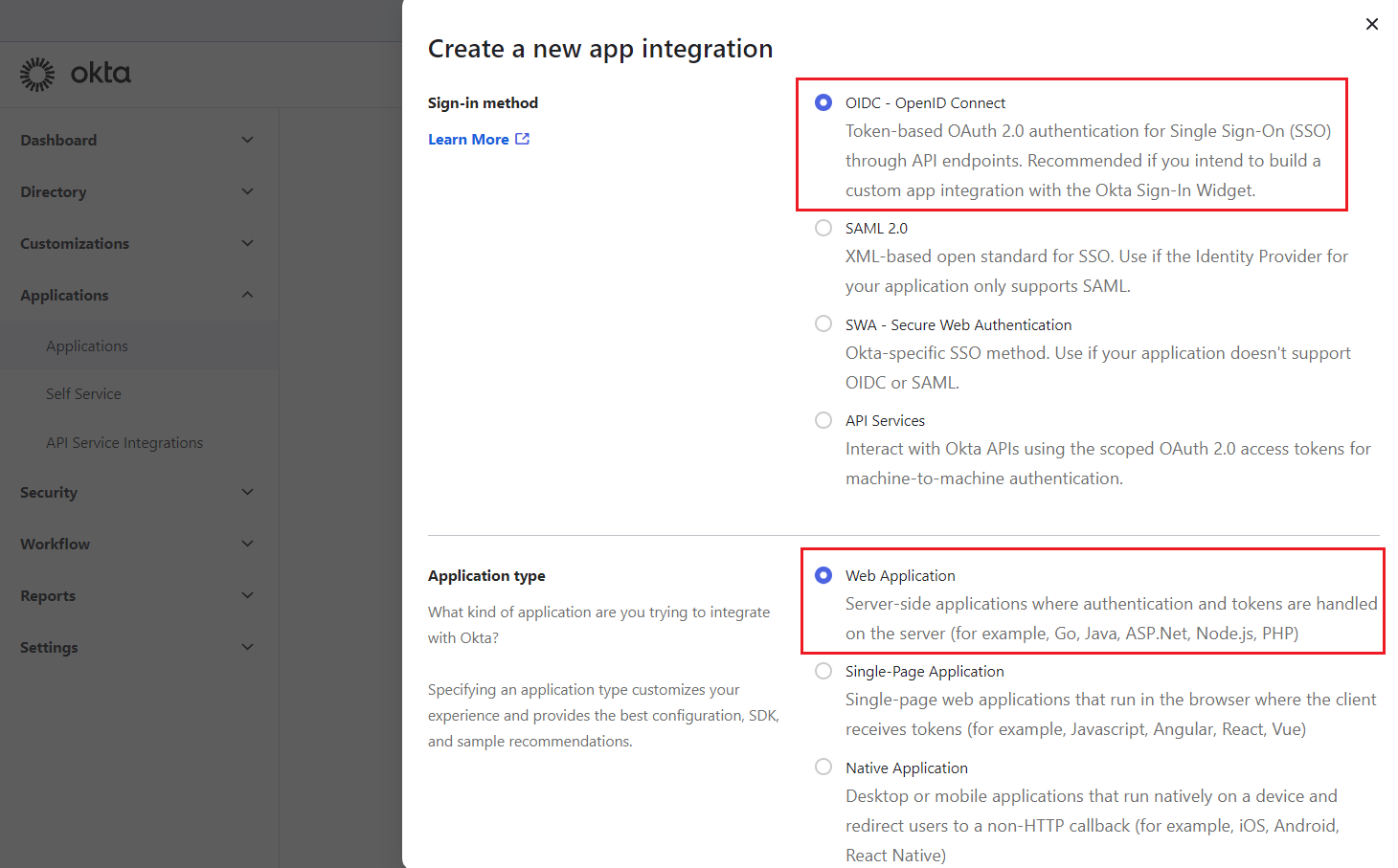
- Enter an App integration name and ensure that Authorization Code is checked. Then, in the Sign-in redirect URLs, enter:
https://login.puredome.com/oauth2/callback
- Under the Assignments section, select Skip group assignment for now. Click Save.
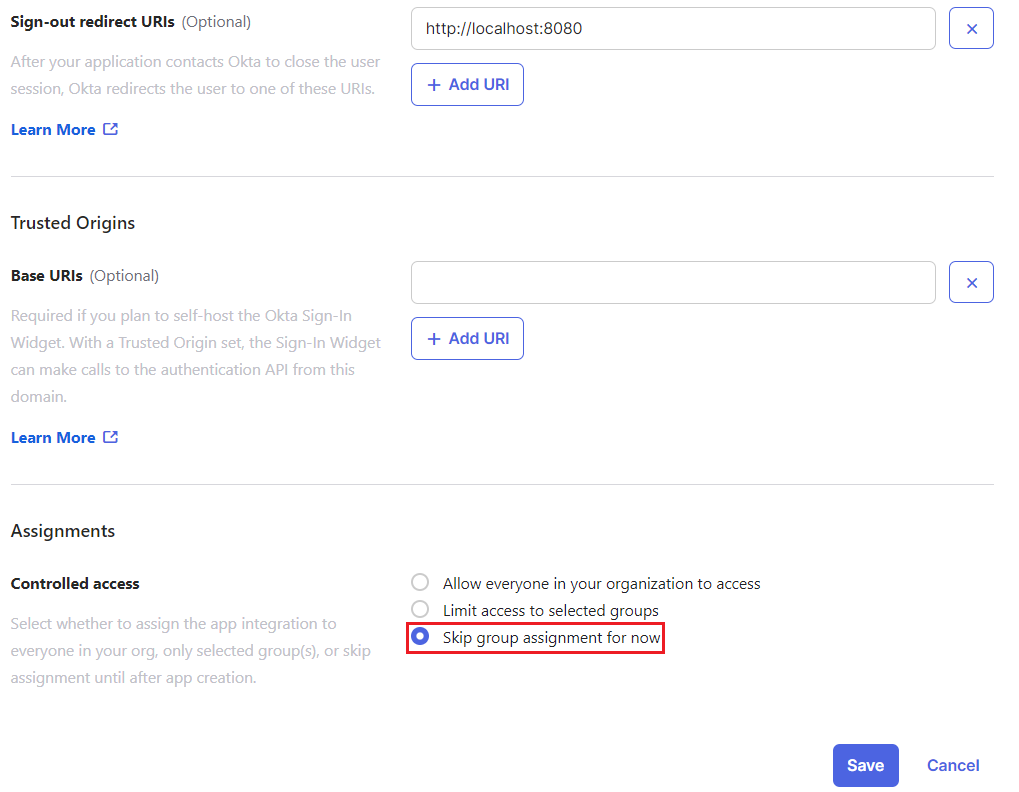
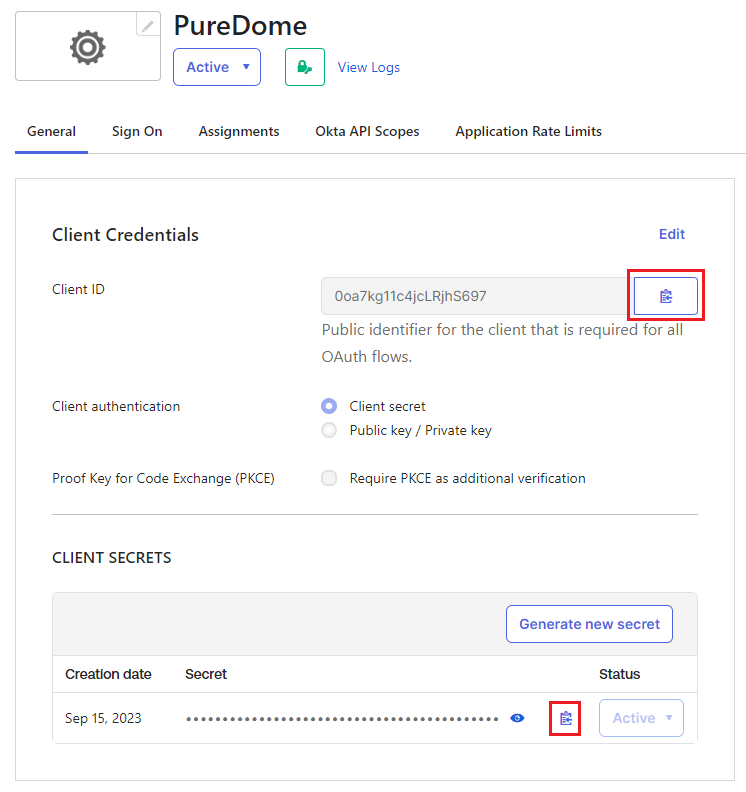
Step 2 - Configuring the Client ID and Client Secret
- Go to the General page of the application that you've just created. Copy Client ID and Client Secret values for later use.
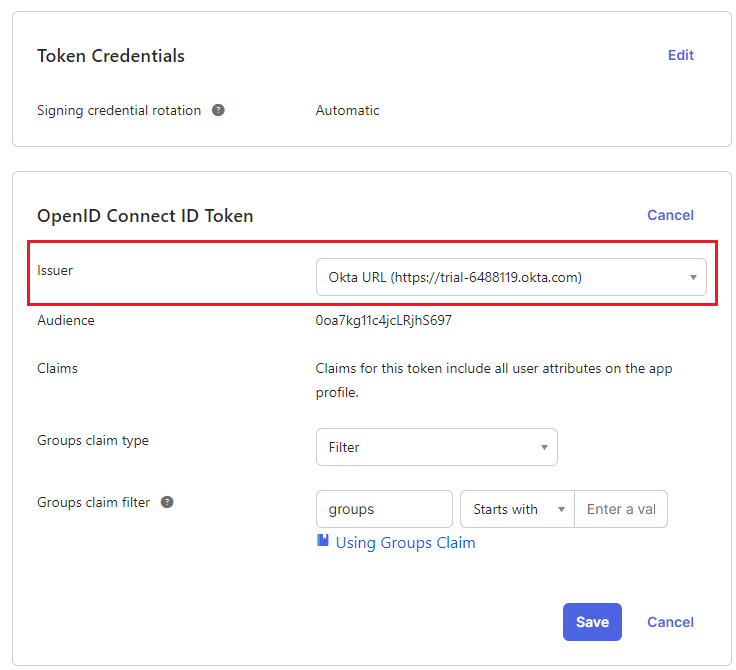
Step 3 - Configuring the Issuer URL
- Under Sign On, navigate to the section OpenID Connect ID Token and change the Issuer to use the Okta URL. Click Save, and copy this URL into a text file for later use.
Step 4 - Managing user access
- Navigate to the Directory section, select People, and choose the username of the user you wish to authenticate. Next, click on Assign Applications, choose the application you've generated, and click Assign. Finally, wrap it up by clicking Save and Go Back and then Done.
Step 5 - Adding a new identity provider
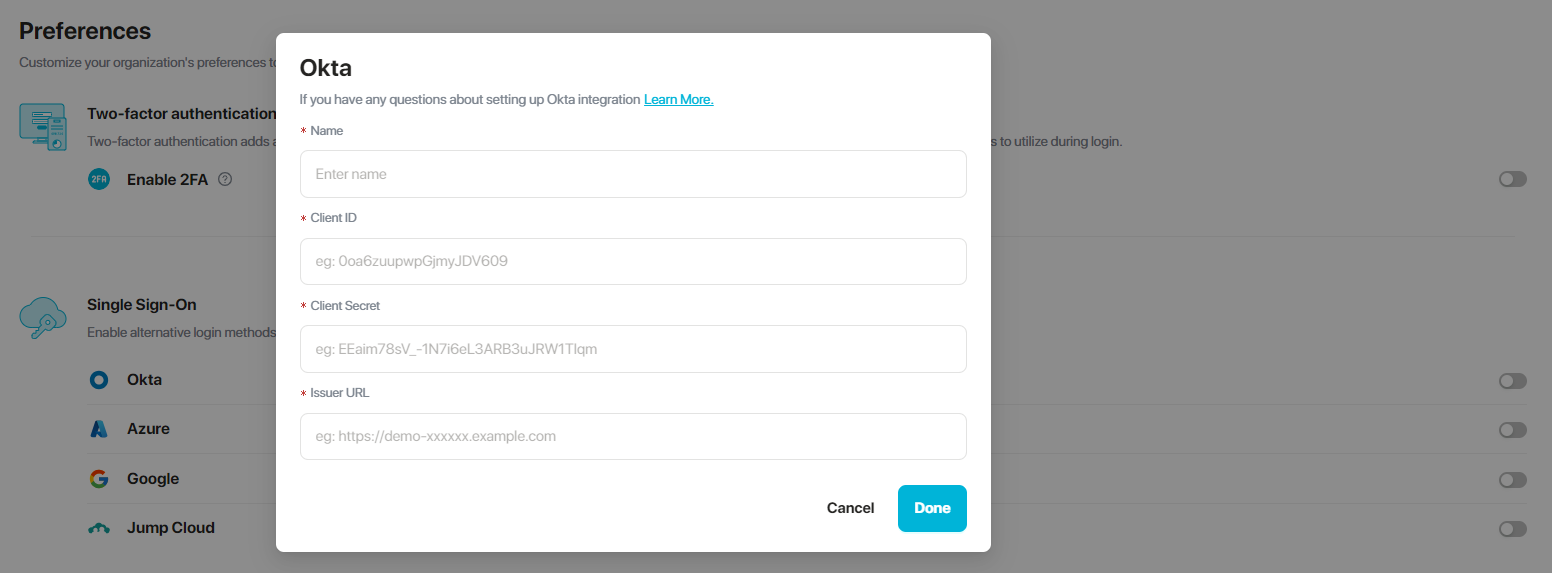
- Now, you can head to the PureDome console on your browser, navigate to Preferences and Single Sign-On. By choosing Okta you will be asked to enter four values as follows:
- IDP Name: Any name you want
- Client ID: Value copied from OKTA dashboard
- IDP Client Secret: Value copied from OKTA dashboard
- Issuer URL: Value copied from OKTA dashboard
- After completing all the steps above, you have successfully set up an OIDC application on your Okta with SSO enabled for PureDome.
How to enable Okta SCIM?
Below are the steps to configure Okta SCIM integration:
Step 1 - Setting Up SCIM in the PureDome Console
- After enabling SCIM, you will find the SCIM Base URL and OAuth Bearer Token values in their respective tabs. Be sure to copy these values for future use.

- In the SCIM section, you’ll also see options for auto-assigning and auto-purchasing licenses. If you’d like, go ahead and enable those features!
Step 2 - Setting up Secure Web Authentication (SWA) Application on Okta
- Log in to Okta and navigate to the Admin panel.

- Navigate to Applications > Applications and click the Create App Integration button.

- Select SWA - Secure Web Authentication and then click Next.

- Enter an App name. Then, in the App's login page URL, enter:
https://login.puredome.com/oauth2/callback
- Under How will your users sign in? section, select Administrator sets username and password & Email from Who sets the credentials and Application username drop down menu, and then click Finish.

Step 3 - SCIM Integration Setup Process
- Go to the General page of the application that you've just created, and then click Edit under App Settings.

- Check the box to Enable SCIM provisioning, and then click Save.

- Go to the Provisioning page of your application, and then click Edit under SCIM Connection.

- Enter/ select the following details, then click Test Connector Configuration:
- SCIM connector base URL: You'll find this in the PureDome console under the SCIM > SCIM Base URL tab after you create the SSO integration and enable SCIM.
- Unique identifier field for users: userName
-
Supported provisioning actions:
- Import New Users and Profile Updates
- Push New Users
- Push Profile Updates
- Authentication Mode: You'll find this in the PureDome console under the SCIM > OAuth Bearer Token tab after you create the SSO integration and enable SCIM.

- If everything in the app is configured correctly, you will receive a successful notification. After that, click Save.

- Go to the Provisioning page of your application. Under Settings, click To App, and then click Edit.

- Check the boxes for Create Users, Update User Attributes, and Deactivate Users, and then click Save.

Step 4 - Managing user access
- Head to the Assignments section of your SCIM application, and select Assign. From there, you can choose to assign it to either individual users or groups. Once you've linked the application from Okta to either specific users or groups, return to the PureDome console. You'll see a list of users with the status "Inactive." Choose the users you want to give licenses to. Then, click Assign License to apply the licenses.

- Or if you aim to sync an entire Okta group to PureDome as a team, remember to add it under the Push Groups tab as well.

Note:
- Single-Sign-On (SSO) will be enabled for the PureDome console and apps.
- Only users/ groups assigned in your organization to this application can log in subject to being invited to the PureDome console via their registered email address on their Okta account.
Note:
Supported app versions for SSO:
Windows: v2.1.6.8 and above
macOS: v2.1.3 and above
iOS: v2.1.2 and above
Android: v2.4.34 and above
If you have any questions or are experiencing any issues, please don't hesitate to contact our 24/7 customer support team via live chat or email at support@puredome.com. We're always happy to help!