MikroTik routers provide an ingenious solution to internet users at home, allowing them to set up several small access points instead of one big one. Because Internet security is a problem with any Wi-Fi device out there, a VPN is always recommended. You can learn how to set up PureVPN on Mikrotik Router from here.
Because Internet security is a problem with any Wi-Fi device out there, a VPN is always recommended. You can learn how to set up VPN on the Mikrotik router from here.
Find your VPN credentials for manual configuration
To find your VPN credentials log into the PureVPN Member Area. Click 👉 here to visit Member Area.
- Login to the Member Area using your PureVPN registered email address and password.
- On Subscription tab scroll down to be able to view your VPN credentials.
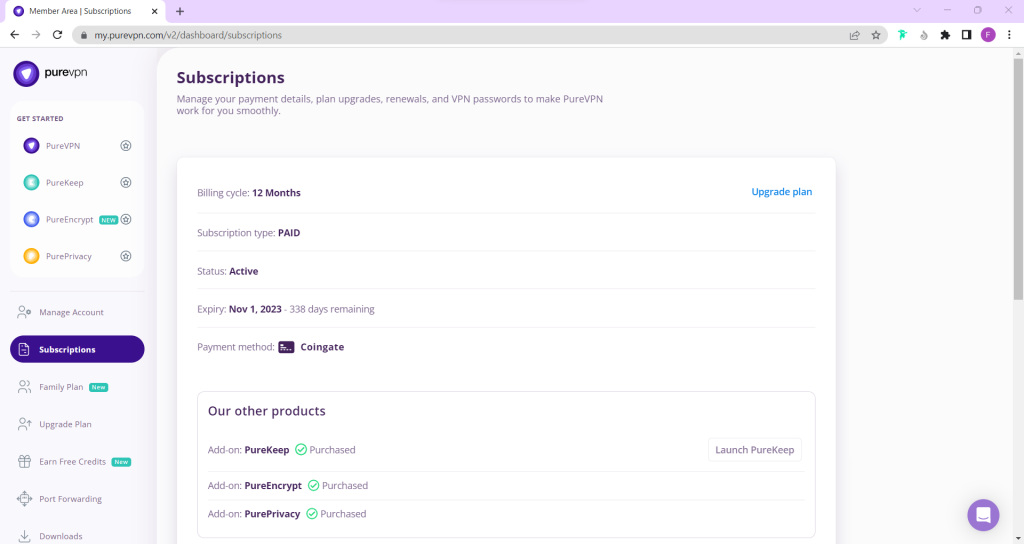
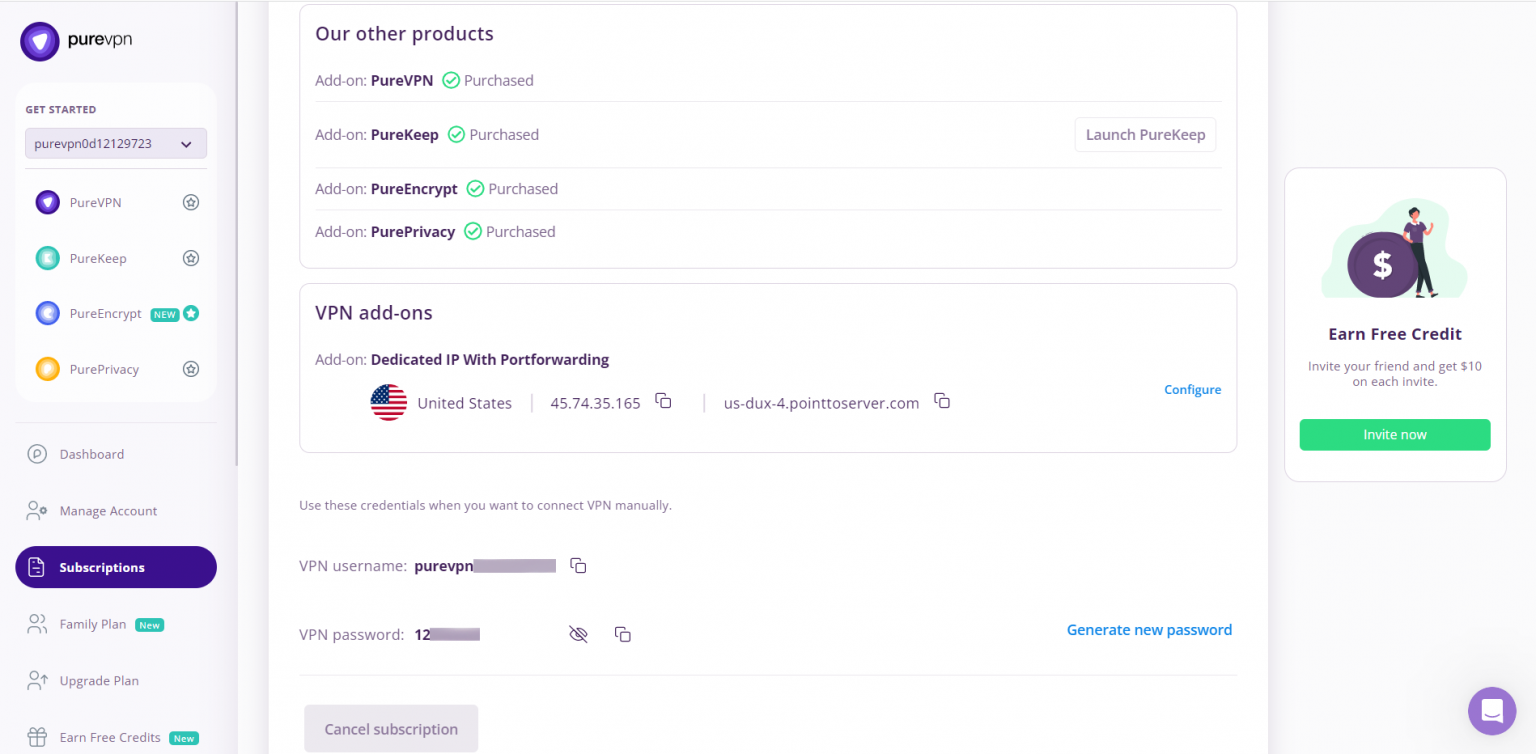
- You will be able to see and copy your VPN credentials.
- Note down your PureVPN username and click the Eye icon to make your password visible and use it in the manual configuration.
How to set up IKEv2 on Mikrotik router
This guide offers a comprehensive step-by-step tutorial for setting up an IKEv2 connection on Mikrotik using PureVPN settings. Follow our instructions to complete your Mikrotik VPN client setup and ensure that your online experience is private, secure, and free from restrictions when using our service.
- Click here to download the certificate.
- Proceed to your Mikrotik configuration panel.
- Open Files and add the certificate you’ve downloaded.
- Import your certificate via System > Certificates > Import. In the drop down menu opposite the Only File field choose the certificate you’ve just added, and click Import.
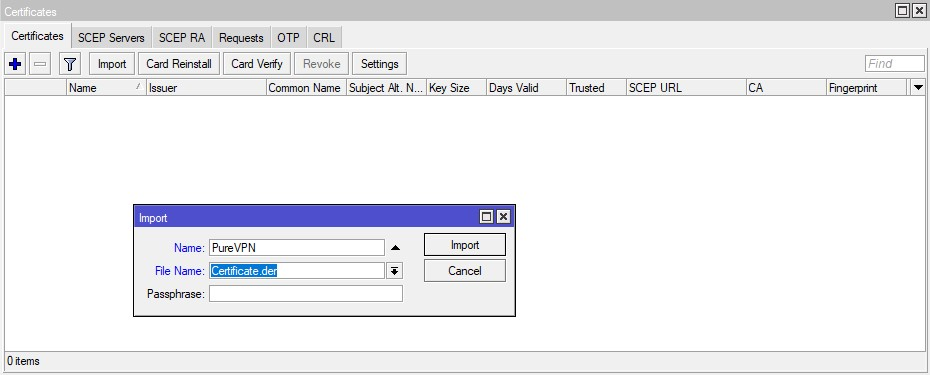
- Add a new profile on your Mikrotik router by navigating to IP > IPsec > Profiles > Add New. Fill out the fields of your new profile in the following way:
- Name: Enter a custom name of your new VPN profile
- Hash Algorithms: sha256
- Encryption Algorithm: aes-128/ aes-256
- DH Group: modp1024/ modp2048
- Proposal Check: obey
- Lifetime: Leave the default 1d 00:00:00
- DPD Interval: 120
- DPD Maximum Failures:
- Click Apply > OK.
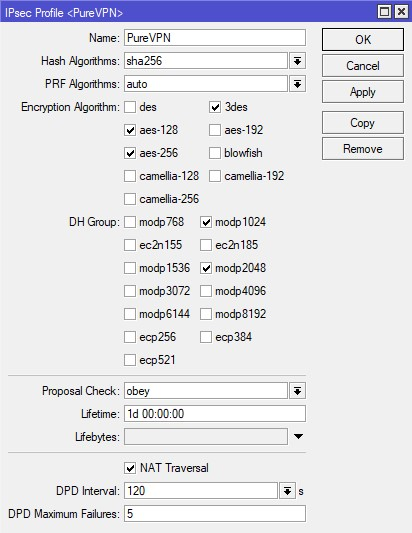
- On the same IPsec screen, go to the Proposals tab and click Add New. Complete the fields as shown below:
- Enabled/Disabled: The button should be enabled.
- Name: Enter a custom name, for example PureVPN
- Auth. Algorithms: sha256
- Enc. Algorithms: aes-128-cbc/ aes-256-cbc/aes-256 gcm
- PFS Group: modp1024
- Click Apply > OK.
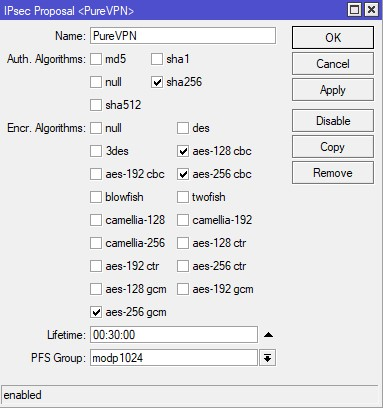
- Navigate to the Groups tab, press Add New, and enter name of the new group, for example PureVPN, and click OK.
- Now you need to create an IPsec policy on your Mikrotik router. Go to the Policies tab and click Add New. Fill out the fields as shown below and click OK:
- Enabled: The box should be checked
- Src. Address: Leave the default 0.0.0.0/0
- Dst. Address: Leave the default 0.0.0.0/0
- Protocol: 255 (all)
- Template: Check the box
- Group: default (make sure it's the one you created in Step 6, in our case it is PureVPN)
- Action: encrypt
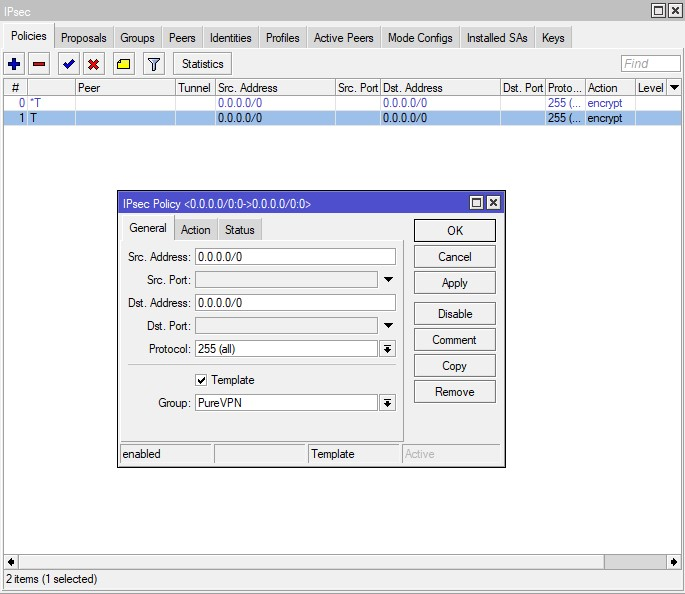
- Proceed to the Mode Configs tab in the same IPsec section and press Add New. Enter the name of the configuration and uncheck the responder select Use Responder DNS: exclusively then click Apply > OK.
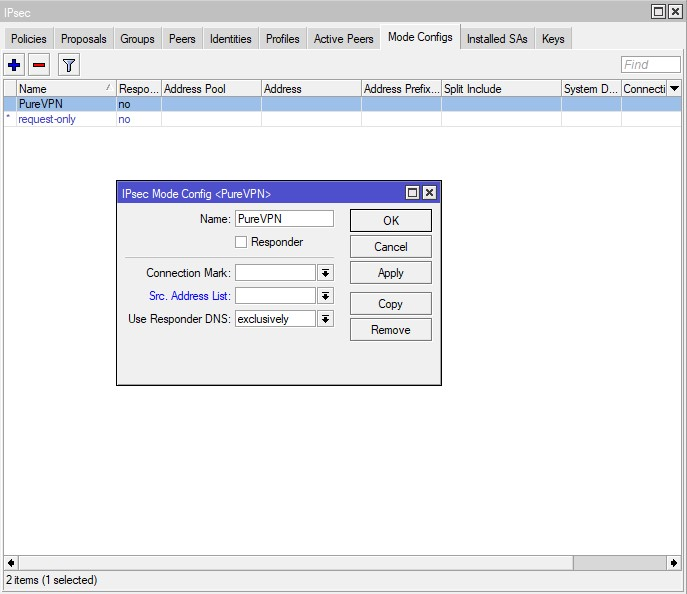
- Create an IPsec peer on the IPsec > Peers tab. Click Add New and provide the following details and click Apply > OK.
- Enabled: The box should be checked
- Address: Enter the Server address of the chosen VPN server
- Profile: Select the created profile, in our case it is PureVPN
- Exchange Mode: main
- Send INITIAL_CONTACT: The box should be checked.
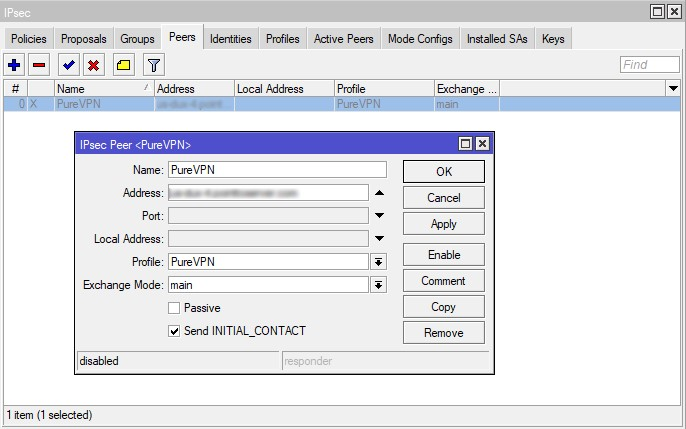
- On the IPsec > Identities tab, click Add New and fill out the fields as shown below:
- Enabled: The box should be checked
- Peer: Select the peer you’ve added, e.g. PureVPN
- Auth. Method: pre shared key xauth
- Secret Key: 12345678
Enter your PureVPN credentials. Here is how you can find your VPN credentials. - Policy Template Group: Select the policy you’ve created, in our example it is PureVPN
- My ID Type: auto
- Remote ID Type: auto
- Remote ID: pointtoserver.com
- Match By: remote id
- Mode Configuration: Choose the name of the configuration you’ve added in step 8
- Generate Policy: port strict
- Click Apply > OK.
- To send all traffic to the tunnel, you need to create an address list with your local network. For this, navigate to Firewall > Address Lists and click Add New. In the Name field, choose your local network and type in its IP address and network prefix length in the Address field.
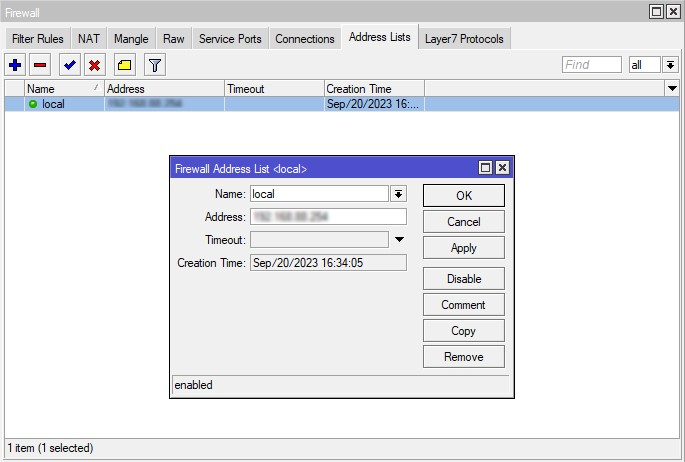
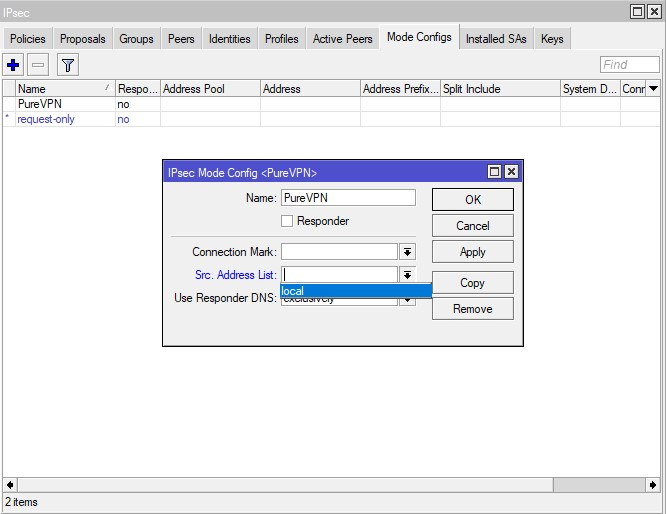
- Now you need to assign this list to your mode configuration. For this, go to IPsec > Mode Configs > PureVPN, and select the list you’ve just created in the drop down menu in front of Src. Address List field.
Note: Don't forget to disable the Fast Track rule in Firewall > Filter Rules list.
- You can check the established connections on the Active Peers tab of the IPsec section.
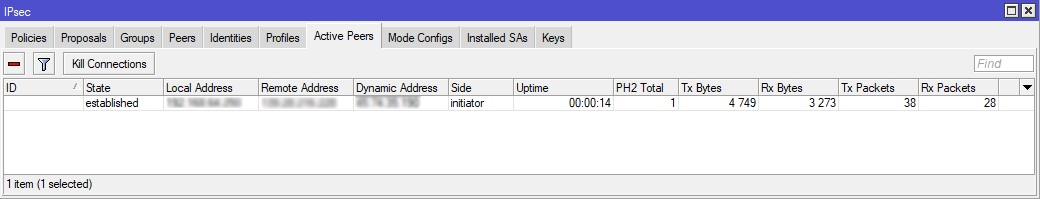
That's about it. Enjoy total unlimited internet freedom with PureVPN!